In this article we are going to look at configuring a VPN to connect remotely to our work if we have a Fortigate Firewall.
What is a VPN?
A VPN (Virtual Private Network) is a private and at the same time encrypted connection that is made through the Internet, to create a private connection or network within the public network that is the Internet.
Typically VPN connections can be:
- Site to Site: Connection between different company headquarters.
- Site to Client: Private connections from computers, mobile phones and tablets to our company.
In this article we are going to look at client connections.
Let’s imagine that we work in a company and we want to connect remotely and securely. To do this, we will use a small software that will make this connection. Once connected to our company and depending on the VPN configuration, we will have access to our entire company or to certain resources (Servers, network segments,…)
What type of VPN Client are there?
Next we are going to see what types of VPN Client exist. Basically there are 2 types of VPN Client connections:
-
IPSec VPN Client
These connections use the IPSec protocol, these connections are the most common and can be configured on most routers and firewalls that have VPN functions. The only drawback is that they use UDP ports (4500 and 500), so if we are in a hotel or connected to a network with restrictions, we will not be able to connect.
-
SSLVPN Client
These connections use port 443, so we will not have Wi-Fi connection restrictions, since the standard https navigation port is used.
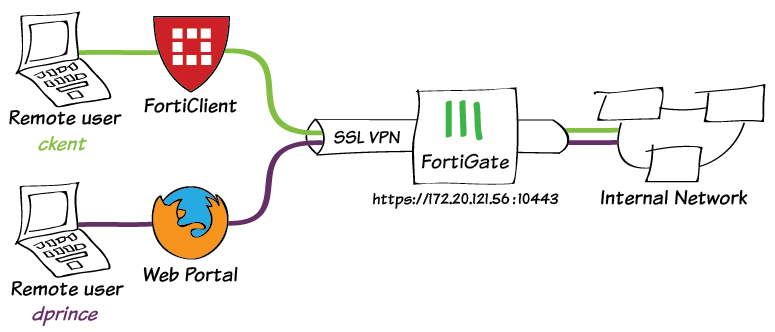
SSL-VPN Fortigate.
How to configure an SSLVPN in Fortigate?
Before starting to configure the SSLVPN, we have to ensure that we have port 443 redirected to the IP of our Firewall that connects to the Internet router.
Once we have our Fortigate configured to browse, we will have to follow the following steps to enable the SSLVPN connection from anywhere outside our office:
- Configure User
- We go to the User & Device -> User Definition and we add a new user
- Configure SSLVPN Portal
- We access the VPN menu -> SSL-VPN Portals and we added a new portal
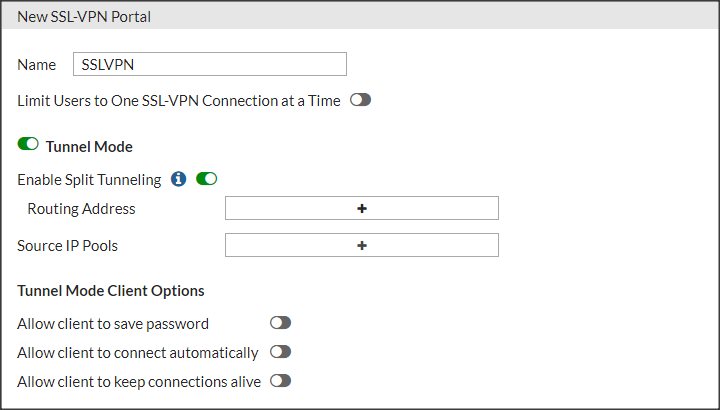
-
- We will only fill in the following fields
- In Routing Address we will put the range or equipment to which we want to have access.
- In Source IP Pools we will leave the default range that Fortigate has, this is SSLVPN_TUNNEL_ADDR1. It is the IP that our computer’s VPN interface will have once we connect via VPN.
- Next we access the VPN menu-> SSL-VPN Settings
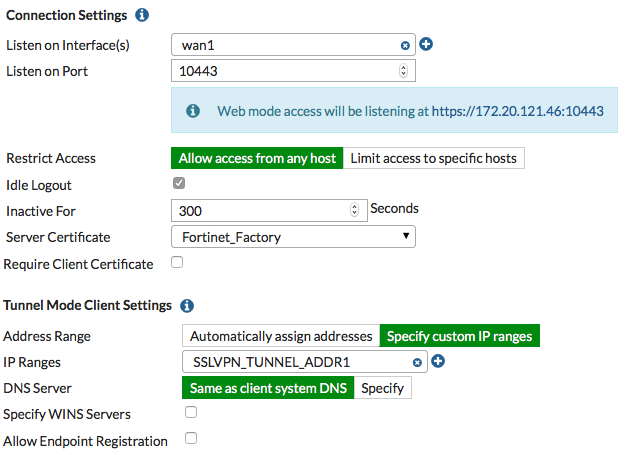
-
- We choose the Internet interface that we have configured.
- In the port we will put port 443 (to avoid blocking public Wi-Fi connections)
- Finally we will map our user, with the portal that we have created
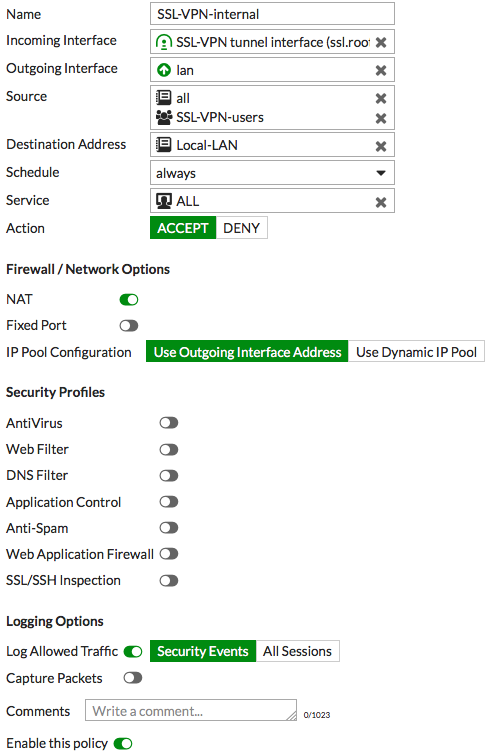
- Configure firewall policy to allow connection from the SSLVPN to our local network.
- Next we have to go to the Policy & Objects -> IPv4 Policy
- We will add a policy to allow entry from the SSLVPN interface with the range SSLVPN_TUNNEL_ADDR1 to our range that we have enabled in the SSLVPN portal configuration. (Routing Address), for the specified user.
Finally we will only have to configure the Forticlient client to make the SSLVPN connection.
From now on you will be able to enjoy completely secure connections to your company with the peace of mind that no one can capture and, above all, analyze the traffic, since it is encrypted.
The information in this article has been taken from the official Fortigate website, you can find the information in this link.

You can consult more articles related to communication networks through this link.
See you on the networks!






Leave A Comment